Evasive Panda exfiltrates data from cloud services by stealing session cookies
ESET discovered a previously unpublished toolkit used to recover data from various cloud services via stolen session cookies
ESET, a leading proactive threat detection company, has identified a post-compromise toolkit used by Evasive Panda to attack a government entity and a religious organization in Taiwan between 2022 and 2023. This toolkit is capable of recovering data from various cloud services by leveraging stolen web session cookies.
Evasive Panda (also known as BRONZE HIGHLAND, Daggerfly o StormBamboo) is a China-aligned APT group, operating since at least 2012. Evasive Panda targets cyberespionage against countries and organizations that oppose China’s interests through pro-independence movements such as those of the Tibetan diaspora, religious and academic institutions in Taiwan and Hong Kong, and pro-democracy advocates in China. Its cyberespionage operations have also occasionally been observed extending to countries such as Vietnam, Myanmar, and South Korea.
Key points of the investigation
- The CloudScout toolset was detected in Taiwan between 2022 and 2023 on the network of a religious institution and a government entity.
- CloudScout uses stolen cookies, provided by MgBot plugins, to access and exfiltrate data stored on various cloud services.
- ESET analyzed three CloudScout modules, which aim to steal data from Google Drive, Gmail, and Outlook, with at least seven additional modules believed to exist.
- Hardcoded fields in CloudScout web requests to steal Outlook emails suggest that the samples in question were designed for Taiwanese users.
In early 2023, ESET detected Evasive Panda deploying three previously unknown .NET modules (internally named CGD, CGM, and COL) on a government entity in Taiwan. These modules are designed to access public cloud services such as Google Drive, Gmail, and Outlook by hijacking authenticated web sessions. This technique relies on stealing cookies from a web browser’s database and then using them in a specific set of web requests to gain access to cloud services.
Unlike stolen credentials, which can be blocked by security features such as two-factor authentication (2FA) and IP tracking, stolen web session cookies allow the attacker to retrieve data stored in the cloud, directly from the victim’s machine. In 2023, Google published the Device Bound Session Credentials (DBSC) project on GitHub, and in 2024, the App-Bound Encryption feature in Chrome update 127. These are protective measures against cookie-stealing malware such as CloudScout and could render this toolkit obsolete.
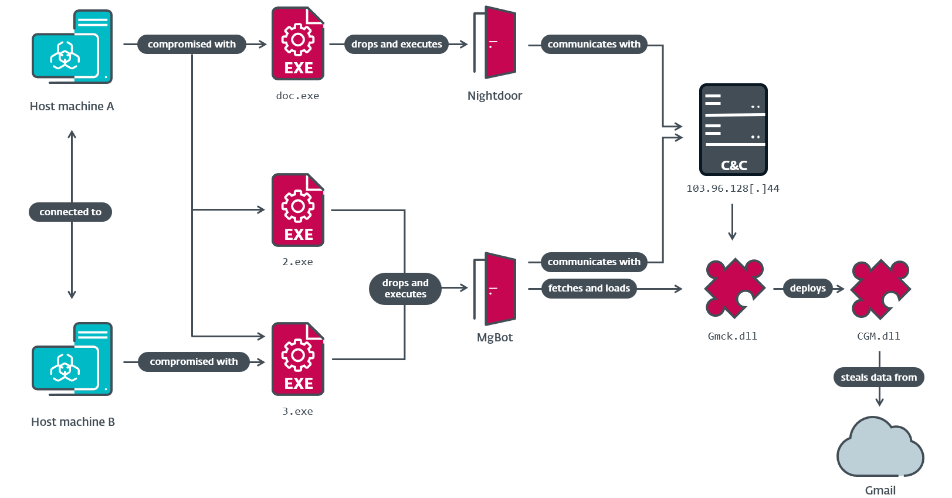
Further analysis of the three modules’ code reveals an underlying development framework, codenamed CloudScout. ESET provides a detailed analysis of this modular framework written in C#, which to our knowledge, and concerning the CloudScout toolkit, has not been previously publicly documented.
According to ESET telemetry, CloudScout was observed in two incidents targeting Taiwan. In May 2022, the network of a Taiwanese religious institution was compromised with MgBot and Nightdoor. In this incident, MgBot was used to install a plugin that deploys a CloudScout module. In February 2023, CloudScout modules and the Nightdoor implant were detected on a suspected Taiwanese government entity. In addition, ESET identified in some hardcoded HTTP requests the inclusion of Taipei Standard Time as a time zone and zh-CN as a language pack. Both suggest that these samples were created to target Taiwanese users.
“At ESET we have highlighted the professional design behind the CloudScout framework to demonstrate Evasive Panda’s technical capabilities and the important role that cloud-stored documents, user profiles and email play in its espionage operations,” concludes Camilo Gutiérrez Amaya from ESET Latin America, regarding the research, its documentation and this controversial topic.
Contact details for ESET: https://www.eset.com/ve/. Also, its social networks: Instagram (@esetla) and Facebook: (ESET).
With information and main reference image provided by Comstat Rowland Comunicaciones Estratégicas Integrales
Visit our news channel on Google News and follow us to get accurate, interesting information and stay up to date with everything. You can also see our daily content on X/Twitter and Instagram


